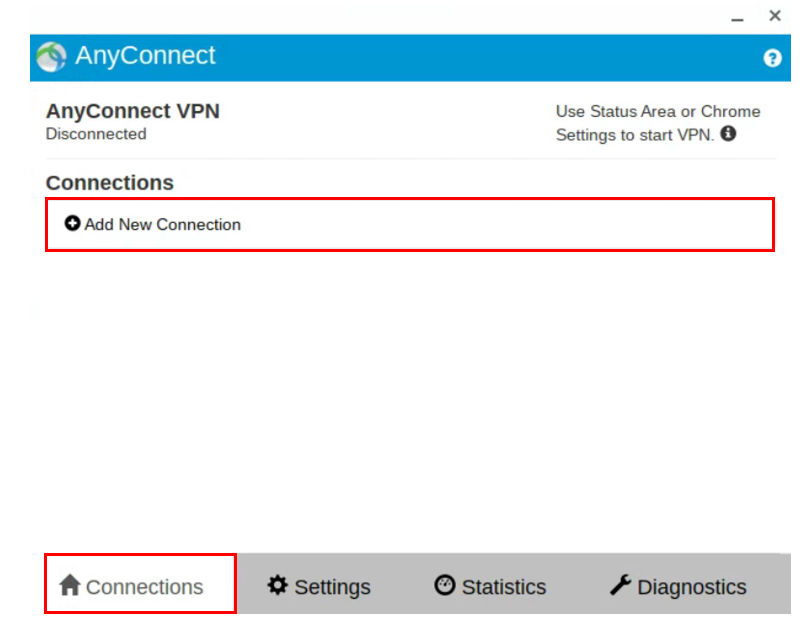
- Download and install the Cisco AnyConnect VPN from the Chrome Web Store.
- Go to Settings in Chrome and create a VPN entry.
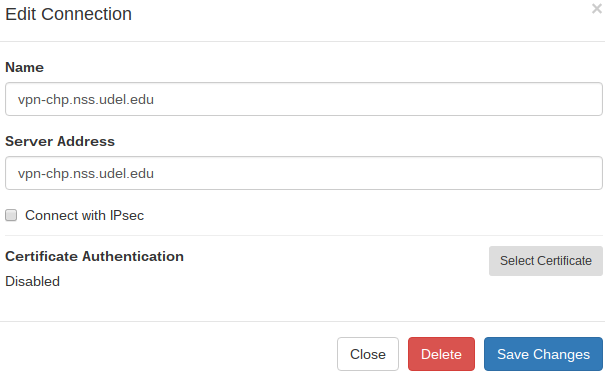
- Connection to Name = UCI
- Server = vpn.uci.edu
- Go to Settings and click on “VPN”, then select “Cisco AnyConnect” and “UCI.”
Compatible with: Windows, Android, iOS, macOS, smart TVs, routers, Chromebook Ive tested 300 VPNs and ExpressVPN is among the 1 last update 2021/04/20 best when it 1 last update 2021/04/20 comes to online activity whether its streaming, torrenting, beating censorship, or surfing securely and anonymously. Install the AnyConnect app from the Chrome Web Store page. Open your quick settings panel by selecting the clock in the corner of the screen.
- Cons: When multiple persons are on it at the same time, the connection can drop and that can create a whole mess.It gives no alert when the connection drops, the only way you know is when you suddenly can't access work files.
- How to setup vpn in ChromeOS in Chromebook fast end easy. Secure SSL VPN connection for ChromeOS will protect you and give an oppotunity to browse anywhere.
- Has anyone used cisco anyconnect with their chromebook. I have been trying to get it to work with our company site and have not had any luck. I also have two coworkers who have similar challenges. Appears we are all being asked for certificates. Yes, we have reached out to our IT team for support.
NOTE: In the near future, OIT will provide an alternate way to login to the VPN using 'SAML authentication'. Due to software limitations, Chromebook users will not be able to use the SAML VPN tunnels. You will need to continue using the standard DEFAULT-UCI or UCIFULL tunnels when connecting to the VPN.
So at some point in time, Cisco stopped supporting 64 bit Linux AnyConnect on the ASA. Or maybe the admin’s on my VPN just don’t have the right plugin, because I know at some point it used to work, or at least on IOS. Gone are the days of the awesome VPN3000 Linux clients I used to use at Cisco that just worked, but I digress.
Enter OpenConnect an Open Source Cisco client, which claims to address a number of deficiencies in the official client:
Vpn Client For Chromebook
- Inability to use SSL certificates from a TPM or PKCS#11 smartcard, or even use a passphrase.
- Lack of support for Linux platforms other than i386.
- Lack of integration with NetworkManager on the Linux desktop.
- Lack of proper (RPM/DEB) packaging for Linux distributions.
- “Stealth” use of libraries with dlopen(), even using the development-only symlinks such as libz.so — making it hard to properly discover the dependencies which proper packaging would have expressed
- Tempfile races allowing unprivileged users to trick it into overwriting arbitrary files, as root.
- Unable to run as an unprivileged user, which would have reduced the severity of the above bug.
- Inability to audit the source code for further such “Security 101” bugs.

On Ubuntu 12.04 it is in the repos. Be sure to add 32-bit compatibility libraries.
myuser@t400-precise:~$ sudo apt-get install ia32-libs openconnect
Anyconnect For Chromebook
You’ll need to get the Cisco Secure Desktop “spyware” (as they call it on the blog) from a 32 bit install of the AnyConnect which should be in $HOME/.cisco and copy it to your 64bit box.
myuser@t400-precise:~$ tar xzvf cisco.tgz
.cisco/
.cisco/hostscan/
.cisco/hostscan/bin/
.cisco/hostscan/bin/csd
.cisco/hostscan/log/
.cisco/hostscan/log/hostscan.log
.cisco/hostscan/log/csd.log
.cisco/hostscan/log/csd_child.log
.cisco/hostscan/lib/
.cisco/hostscan/lib/libinspector.so.gz
.cisco/hostscan/lib/tables.dat
.cisco/hostscan/lib/libinspector.so
.cisco/hostscan/lib/libhostscan.so
.cisco/hostscan/lib/libcsd.so
.cisco/hostscan/lib/libhostscan.so.gz
.cisco/hostscan/lib/libcsd.so.gz
.cisco/vpn/
.cisco/vpn/cache/
.cisco/vpn/cache/inst.sh
.cisco/vpn/cache/update.txt
Then it is just a matter of figuring out the command line arguments, in particular the –csd-user parameter. For the username and the authentication group it will prompt you.
myuser@t400-precise:~$ openconnect vpn.myvpn.com --csd-user=myuser
Attempting to connect to 1.1.1.1:443
SSL negotiation with vpn.myvpn.com
Connected to HTTPS on vpn.myvpn.com
GET https://vpn.myvpn.com/
Got HTTP response: HTTP/1.0 302 Object Moved
SSL negotiation with vpn.myvpn.com
Connected to HTTPS on vpn.myvpn.com
GET https://vpn.myvpn.com/+webvpn+/index.html
GET https://vpn.myvpn.com/CACHE/sdesktop/install/binaries/sfinst
GET https://vpn.myvpn.com/+CSCOE+/sdesktop/wait.html
Refreshing +CSCOE+/sdesktop/wait.html after 1 second...
csd.linux.i386
GET https://vpn.myvpn.com/+CSCOE+/sdesktop/wait.html
Refreshing +CSCOE+/sdesktop/wait.html after 1 second...
GET https://vpn.myvpn.com/+CSCOE+/sdesktop/wait.html
Refreshing +CSCOE+/sdesktop/wait.html after 1 second...
GET https://vpn.myvpn.com/+CSCOE+/sdesktop/wait.html
Refreshing +CSCOE+/sdesktop/wait.html after 1 second...
GET https://vpn.myvpn.com/+CSCOE+/sdesktop/wait.html
Got HTTP response: HTTP/1.1 302 Moved Temporarily
GET https://vpn.myvpn.com/+webvpn+/index.html
Please enter your username and password.
GROUP: [SSL]:SSL
Username:myuser
Password:
POST https://vpn.myvpn.com/+webvpn+/index.html
Got CONNECT response: HTTP/1.1 200 OK
CSTP connected. DPD 30, Keepalive 20
TUNSETIFF failed: Operation not permitted
myuser@t400-precise:~$ sudo openconnect vpn.myvpn.com --authgroup=SSL -u myuser --csd-user=myuser
Attempting to connect to 1.1.1.1:443
SSL negotiation with vpn.myvpn.com
Connected to HTTPS on vpn.myvpn.com
GET https://vpn.myvpn.com/
Got HTTP response: HTTP/1.0 302 Object Moved
SSL negotiation with vpn.myvpn.com
Connected to HTTPS on vpn.myvpn.com
GET https://vpn.myvpn.com/+webvpn+/index.html
GET https://vpn.myvpn.com/CACHE/sdesktop/install/binaries/sfinst
GET https://vpn.myvpn.com/+CSCOE+/sdesktop/wait.html
csd.linux.i386
Refreshing +CSCOE+/sdesktop/wait.html after 1 second...
GET https://vpn.myvpn.com/+CSCOE+/sdesktop/wait.html
Refreshing +CSCOE+/sdesktop/wait.html after 1 second...
GET https://vpn.myvpn.com/+CSCOE+/sdesktop/wait.html
Refreshing +CSCOE+/sdesktop/wait.html after 1 second...
GET https://vpn.myvpn.com/+CSCOE+/sdesktop/wait.html
Got HTTP response: HTTP/1.1 302 Moved Temporarily
GET https://vpn.myvpn.com/+webvpn+/index.html
Please enter your username and password.
Password:
POST https://vpn.myvpn.com/+webvpn+/index.html
Got CONNECT response: HTTP/1.1 200 OK
CSTP connected. DPD 30, Keepalive 20
Connected tun0 as 192.168.10.45, using SSL
No --script argument provided; DNS and routing are not configured
DTLS handshake failed: 5

You’ll have to add the routes you need and send then to the tun0 interface either manually or with the script command.
Cisco Anyconnect Chromebook
Simple eh?
